The Singapore Police Force and crypto security companies have warned of a recent pattern of crypto wallet drainer attacks. The hackers use a sophisticated combination of phishing campaigns and a smart contract to gain access to victims’ crypto before draining them dry.
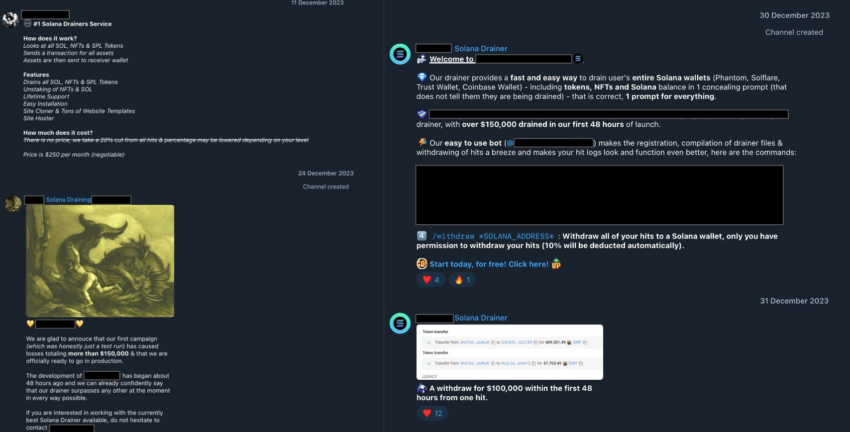
The crypto scam has been perpetrated by Drainer-as-a-Service software peddled by more sophisticated actors.
How the New Crypto Wallet Drainer Scam Works
According to authorities in Singapore, the criminals first infiltrate a legitimate account on a platform such as X. They then entice users to click on a link directing them to a malicious website.
Hackers then get the user to connect their crypto wallet to the site and authenticate their account with private keys. Once they perform these tasks, the hacker asks the victim to interact with a smart contract under the pretext of claiming their free tokens.
The interaction with the smart contract then gives hackers full access to the victim’s funds. The criminals then drain assets and send them to a crypto mixer, making them hard to trace.
Read more: How To Identify a Scam Crypto Project
The attack involves the use of a sophisticated Drainer-as-a-Service software kit. In some cases, less-sophisticated attackers use these services in exchange for a portion of the criminal proceeds.
Sometimes, the sellers require payments in crypto assets like Bitcoin. By far, most bad actors still favor Bitcoin over other crypto assets as a payment method on the darknet, according to Chainalysis.
Crypto Security Companies Sound Alarm
Several crypto security firms say the number of malicious drainer applications is increasing. One community of Solana wallet drainers reportedly had 6,200 users as of earlier this month. CertiK and Blockaid have expressed concern about these thriving communities.
“These drainers are highly sophisticated and can deceive the simulations used by Solana wallets, leading users to unknowingly sign malicious transactions.”

CertiK confirmed that funds lost to crypto scams in 2024 totaled $77 million. The CEO of Ripple Labs, Chris Larsen, confirmed that several of his crypto accounts had been compromised yesterday.
Read more: Top 10 Must Have Cryptocurrency Security Tips
A recent attack affecting Ledger Connect Kit users used a supply chain method to compromise the wallet. In this type of attack, the hacker finds a weakness in one or more of a product’s components.
In the case of Ledger, the attacker injected a malicious wallet drainer payload into the @ledgerhq/connect-kit NPM software component. This payload gave them access to all the decentralized applications the user linked to their wallet.
Another attack vector involves stealing a crypto user’s mobile number to gain access to crypto applications. In this attack, the criminal convinces mobile operators that they are real customers who must move their numbers to an alternative mobile SIM card.
The operator then transfers the number from the legitimate holder to the criminal. Authorities recently charged a California man named Robert Powell with operating a SIM-swap ring that allegedly stole $400 million in crypto and fiat.
![]()
PrimeXTB
Explore →
![]()
DeGate
Explore →
![]()
AlgosOne
Explore →
![]()
Wirex App
Explore →
![]()
KuCoin
Explore →
![]()
Margex
Explore →
Explore more
The post Singapore Raises Red Flags: Concerns Over Crypto Draining Kits Emerge appeared first on BeInCrypto.




